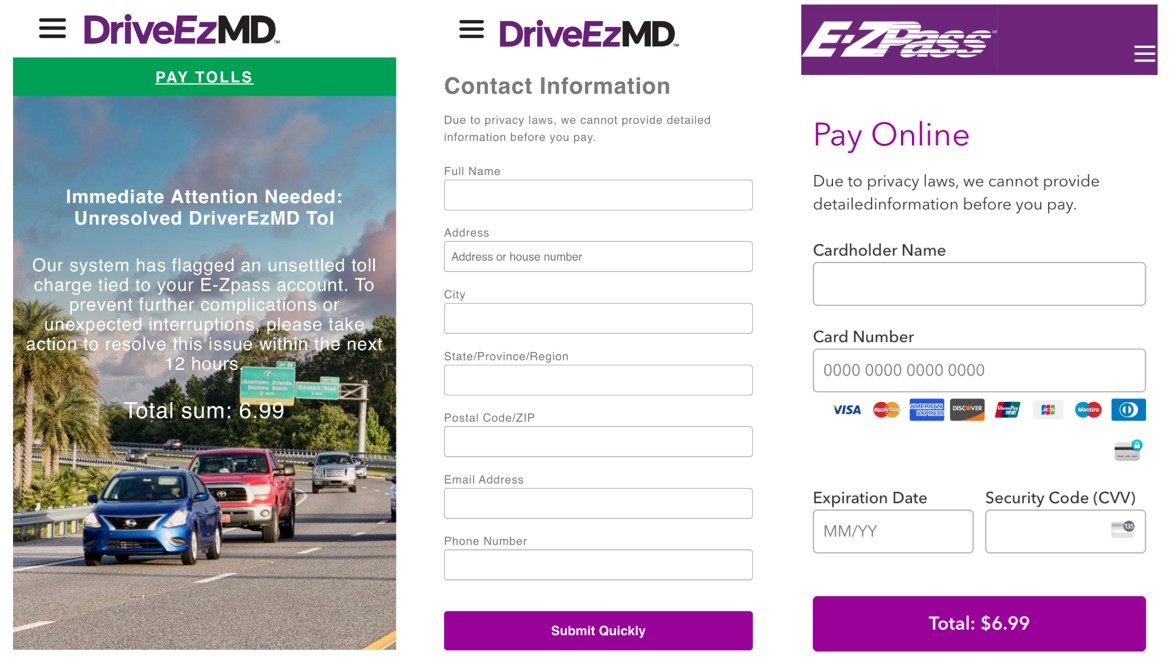
Scammers are cloning official government websites, including the FBI’s own cybercrime portal, to steal personal and financial data from unsuspecting residents, prompting a new nationwide warning from the bureau. These lookalike sites often appear in search results or online ads and can be nearly indistinguishable from the real thing at a glance.
What the FBI Is Warning About
The FBI has issued a Public Service Announcement detailing how threat actors are spoofing the Internet Crime Complaint Center (IC3) website, the central hub where victims report cybercrime. Cybercriminals copy the design, language, and branding of the legitimate portal, then lure residents to fake versions to harvest sensitive information.
Officials stress that these sites are not minor nuisances but part of coordinated campaigns to commit identity theft, financial fraud, and follow‑on scams. In some cases, fake IC3 sites and related phishing pages are even promoted through sponsored search results or misleading links shared via email and social media.
How Fake Government Sites Work
Spoofed government websites typically rely on small but critical domain name changes, such as subtle misspellings, extra words, or different top‑level domains like “.com” or “.org” instead of “.gov.” Once a victim lands on the fake page, it may display familiar government seals, fonts, and color schemes to build trust.
These fraudulent portals then prompt users to submit highly sensitive personal details, including full name, home address, phone number, email, and sometimes banking information under the guise of “verification” or “case review.” The stolen data can be used to open fraudulent accounts, orchestrate wire transfer schemes, or fuel more targeted phishing attacks that appear to come from real agencies.
Spotting a Fake Government Website
Residents can dramatically reduce their risk by taking a few verification steps before entering any information on a government site.
Key checks include:
- Manually typing known addresses into the browser (for IC3, the only legitimate URL is **www.ic3.gov**).
- Confirming that the address ends in “.gov” and matches the official URL exactly, without extra characters or alternate spellings.
- Being cautious of “sponsored” search results or ads that appear above organic listings when searching for government services.
- Watching for low‑quality graphics, unusual pop‑ups, or requests for information that seem overly invasive or unrelated to the service.
If something feels off—such as pressure to act urgently, promises to recover lost funds, or requests for payment in cryptocurrency or gift cards—residents should navigate away and independently contact the agency using a verified phone number or URL.
What To Do If You Think You Were Tricked
Anyone who suspects they submitted information to a spoofed government site should act quickly to limit the damage. Recommended steps include notifying banks or credit card providers, changing passwords on affected accounts, and enabling multifactor authentication wherever possible.
The FBI is urging potential victims to report interactions with fake IC3 or other impersonator sites to their local FBI field office and to the real IC3 portal at www.ic3.gov. These reports help investigators track emerging domains, take down fraudulent infrastructure, and warn other residents before they become the next targets.
This structure keeps the message visually simple but authoritative, giving residents a fast way to remember how to verify government sites before they click or share.

