Apple’s Legacy Contact: Family Access For Photos and Data When You Pass On
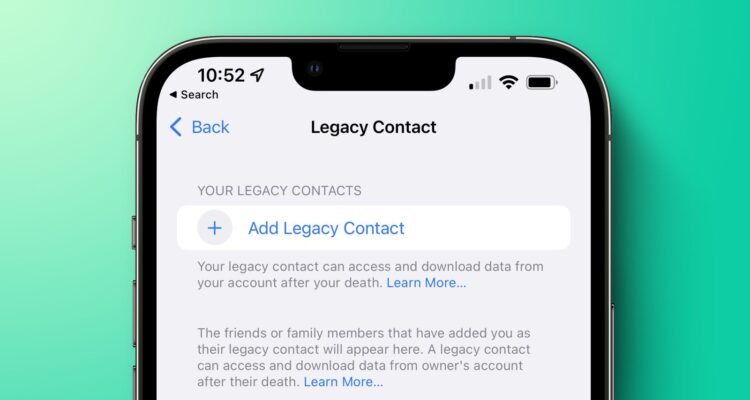
A Legacy Contact is someone you choose to have access to the data in your Apple account after your death. Learn about the information that’s shared with your Legacy Contact and how to add one or more Legacy Contacts HERE